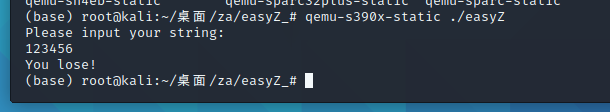
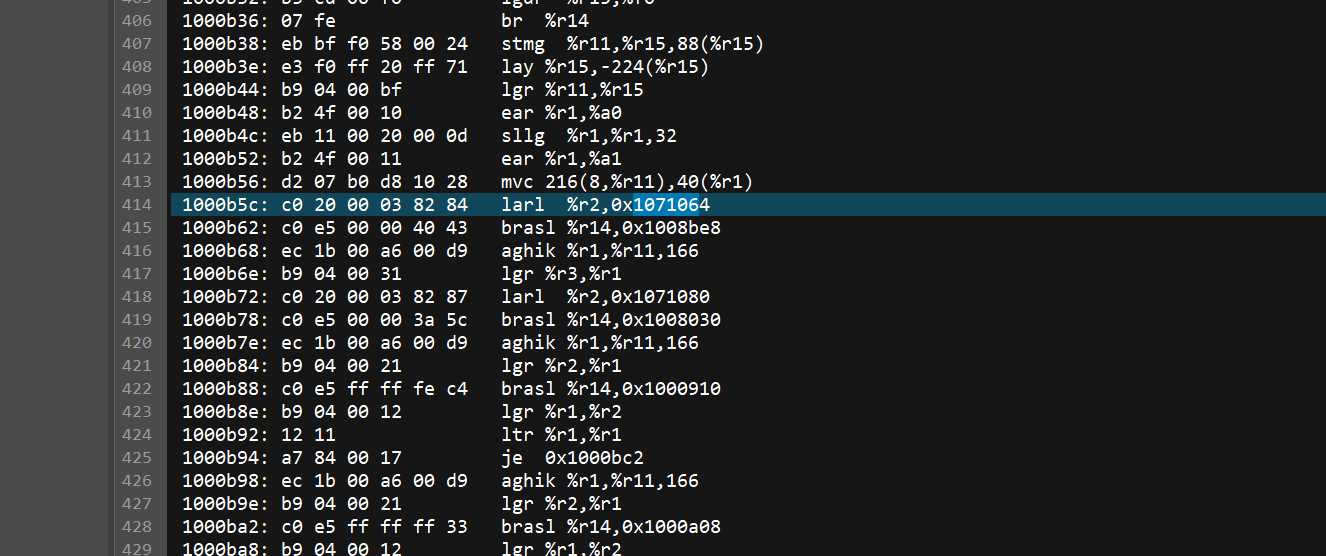
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
|
from __future__ import print_function
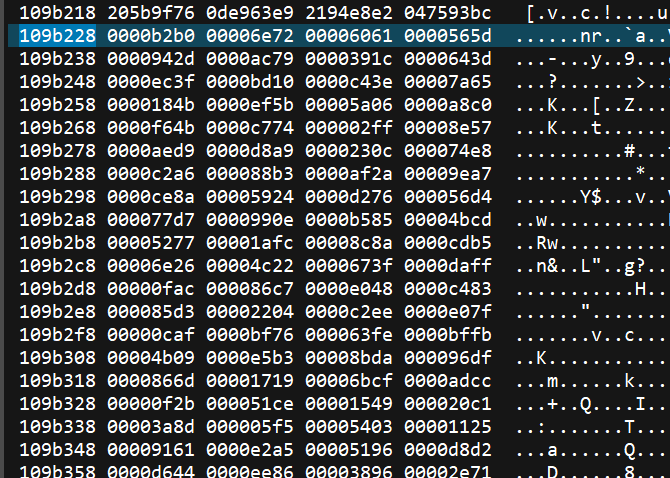
data= [0x0000b2b0, 0x00006e72, 0x00006061, 0x0000565d,
0x0000942d, 0x0000ac79, 0x0000391c, 0x0000643d,
0x0000ec3f, 0x0000bd10, 0x0000c43e, 0x00007a65,
0x0000184b, 0x0000ef5b, 0x00005a06, 0x0000a8c0,
0x0000f64b, 0x0000c774, 0x000002ff, 0x00008e57,
0x0000aed9, 0x0000d8a9, 0x0000230c, 0x000074e8,
0x0000c2a6, 0x000088b3, 0x0000af2a, 0x00009ea7,
0x0000ce8a, 0x00005924, 0x0000d276, 0x000056d4,
0x000077d7, 0x0000990e, 0x0000b585, 0x00004bcd,
0x00005277, 0x00001afc, 0x00008c8a, 0x0000cdb5,
0x00006e26, 0x00004c22, 0x0000673f, 0x0000daff,
0x00000fac, 0x000086c7, 0x0000e048, 0x0000c483,
0x000085d3, 0x00002204, 0x0000c2ee, 0x0000e07f,
0x00000caf, 0x0000bf76, 0x000063fe, 0x0000bffb,
0x00004b09, 0x0000e5b3, 0x00008bda, 0x000096df,
0x0000866d, 0x00001719, 0x00006bcf, 0x0000adcc,
0x00000f2b, 0x000051ce, 0x00001549, 0x000020c1,
0x00003a8d, 0x000005f5, 0x00005403, 0x00001125,
0x00009161, 0x0000e2a5, 0x00005196, 0x0000d8d2,
0x0000d644, 0x0000ee86, 0x00003896, 0x00002e71,
0x0000a6f1, 0x0000dfcf, 0x00003ece, 0x00007d49,
0x0000c24d, 0x0000237e, 0x00009352, 0x00007a97,
0x00007bfa, 0x0000cbaa, 0x000010dc, 0x00003bd9,
0x00007d7b, 0x00003b88, 0x0000b0d0, 0x0000e8bc]
result = [0x08a73233, 0x116db0f6, 0x0e654937, 0x03c374a7,
0x16bc8ed9, 0x0846b755, 0x08949f47, 0x04a13c27,
0x0976cf0a, 0x07461189, 0x1e1a5c12, 0x11e64d96,
0x03cf09b3, 0x093cb610, 0x0d41ea64, 0x07648050,
0x092039bf, 0x08e7f1f7, 0x004d871f, 0x1680f823,
0x06f3c3eb, 0x2205134d, 0x015c6a7c, 0x11c67ed0,
0x0817b32e, 0x06bd9b92, 0x08806b0c, 0x06aaa515,
0x205b9f76, 0x0de963e9, 0x2194e8e2, 0x047593bc]
a = 0
for i in range(32):
for input in range(0x20,0x7e,1):
a = input * input * data[i]+ data[i + 32] * input+ data[i + 64]
if a == result[i]:
print(chr(input),end="")
break
|